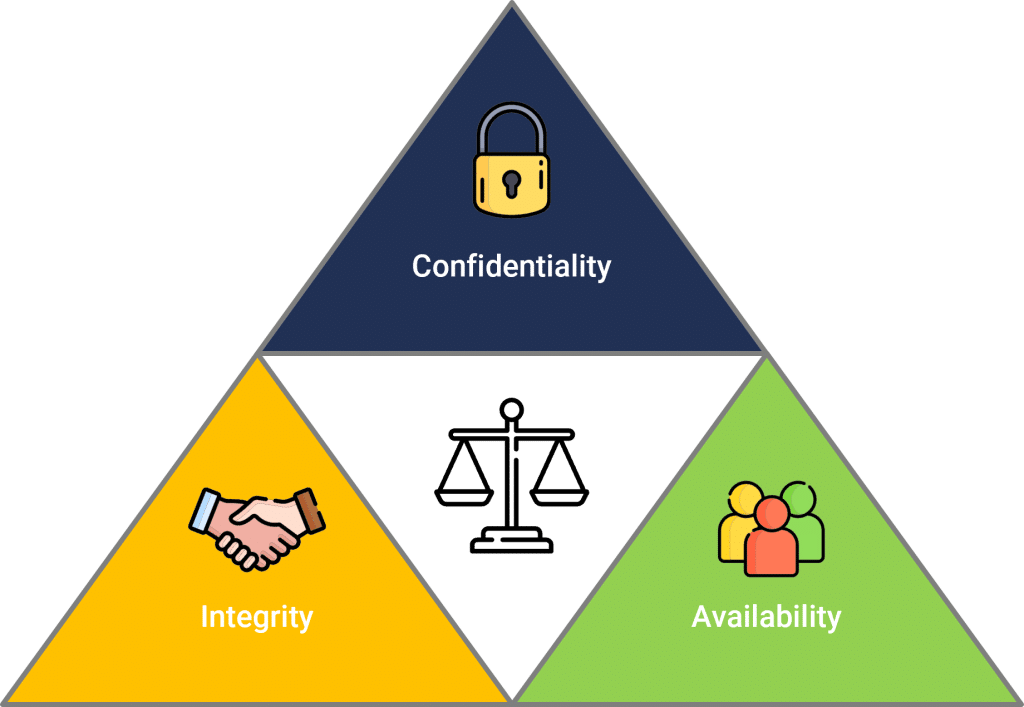
In today’s blog post, we’ll explore the CIA triad, a foundational concept that’s often referred to as the trinity of IT security. The CIA triad stands for Confidentiality, Integrity, and Availability and is a crucial framework for ensuring the protection of data and systems. Let’s dive in and understand each component in detail.
Confidentiality
Confidentiality is all about safeguarding the secrecy of data on our network and IT systems. It involves implementing measures to prevent unauthorized access and disclosure of sensitive information. To achieve confidentiality, organizations employ authentication measures, ensuring that individuals have to authenticate themselves before accessing data. Access control measures are also implemented, both physically and logically, to restrict unauthorized entry. Encryption also plays a vital role in ensuring data confidentiality, providing an added layer of security.
Integrity
Integrity is about maintaining the accuracy and trustworthiness of data. It ensures that data is not modified, tampered with, or corrupted by unauthorized entities. One way to ensure data integrity is through input validation. Organizations employ input validation techniques to ensure that data sent to their web applications adheres to expected formats and prevents malicious code injection. Additionally, creating audit trails enables organizations to log activities and track any modifications or tampering incidents, promoting data integrity.
Availability
Availability focuses on making sure that data, systems, and resources are accessible and functional when needed. Organizations strive to provide uninterrupted services and ensure business continuity. Redundancy measures, such as battery backups, redundant servers, and backup IT systems, are key to maintaining availability. Regular data backups play a critical role in quickly restoring operations if servers fail. It’s important to strike a balance between confidentiality, integrity, and availability, as implementing stringent security measures can often impact the availability of systems and data.
Balancing Act
Maintaining a balance between confidentiality, integrity, and availability is crucial for any organization. IT security teams prioritize confidentiality and integrity, aiming to fortify systems against potential threats. On the other hand, business operations teams prioritize availability to ensure smooth functioning. It’s essential to find the right balance between all three aspects. Organizations must assess their specific requirements and deploy security measures that meet their needs without compromising availability.
Conclusion
The CIA triad, consisting of Confidentiality, Integrity, and Availability, forms the bedrock of IT security. Understanding and implementing measures to uphold these three components is vital for safeguarding data and systems from potential threats. Maintaining the right balance between confidentiality, integrity, and availability ensures that organizations can operate effectively and securely.
If you’d like to delve deeper into the topic, check out my Cyber Security for Absolute Beginners: Essential Concepts or Information Security Management Fundamentals for Non-Techies course. Thank you for reading, and stay tuned for our next blog post.
